A Complete Guide to Secure Hard Drive Recycling for Businesses

When you hear "secure hard drive recycling," what comes to mind? It's not just about dragging old files to the trash icon. We're talking about the complete, irreversible destruction of data on retired hard drives before the physical hardware gets recycled. For any serious organization, whether a local business or a national enterprise, this means using certified methods like Department of Defense (DoD) compliant wiping or turning the drives into tiny metal bits through physical shredding. It’s the only way to guarantee that data is gone for good, keeping you out of the headlines and on the right side of regulators.
Why Secure Hard Drive Recycling Is a Critical Business Function

Treating old hard drives like any other piece of office junk is a massive, and frankly, dangerous oversight. In today's world, having a formal process for destroying data on old drives isn't just "best practice"—it's a non-negotiable part of risk management for companies of all sizes, nationwide. Every single server, laptop, or external drive that's taken out of service is a ticking time bomb of sensitive information, a potential liability just waiting to explode.
From a hospital in Georgia to a data center in Texas, dropping the ball on this final stage of the data lifecycle can have severe, real-world consequences. Bottom line: secure hard drive recycling is an essential part of any strategy for businesses learning how to prevent data breaches and lock down their information when it's most vulnerable.
The Real-World Consequences of Improper Disposal
These risks aren't just hypotheticals we cook up. A single hard drive handled the wrong way can set off a chain reaction of financial, reputational, and legal disasters for any business, anywhere in the US.
- Steep Regulatory Fines: Imagine a hospital misplacing a server drive packed with patient health information (PHI). That one mistake can trigger crippling HIPAA fines that easily run into the millions.
- Irreversible Reputational Damage: Think about a university that auctions off old lab computers without securely wiping student and faculty data. The public scandal could erode trust that took decades to build.
- Loss of Intellectual Property: A data center that decommissions servers without certified destruction could accidentally leak proprietary code or client lists, essentially handing a golden ticket to their competitors.
A documented, proactive approach to data destruction is the only real defense against today's data breach threats and tightening privacy laws. It's time to stop thinking of it as a cost and start seeing it as a strategic investment in your organization's security.
Understanding the Fundamental Approaches
When it comes to securing data at the end of its life, you really have two main paths: data sanitization or physical destruction. The right choice hinges on how sensitive the data is and whether the hardware has any life left in it. We provide both local and nationwide secure hard drive recycling services to meet these needs.
- Data Sanitization (Wiping): This is a software-based approach. Specialized programs overwrite every single sector of a hard drive with random data, often multiple times, making the original information impossible to recover. The big plus here is that it preserves the physical drive, allowing it to be safely reused or resold.
- Physical Destruction (Shredding): This is the final answer. An industrial shredder literally tears the hard drive into mangled, unrecognizable metal fragments. Data recovery isn't just difficult; it's physically impossible. This is the go-to method for drives with highly sensitive information or for hardware that's too old to be useful.
The demand for these services is exploding as more organizations wake up to the stakes involved. The global hard drive destruction service market was valued at a hefty USD 1.65 billion in 2024 and is projected to skyrocket to USD 5.05 billion by 2035. This incredible growth just goes to show how critical certified data destruction has become for fighting off security threats and meeting tough regulations.
Ultimately, a rock-solid secure hard drive recycling program is just one piece of a bigger puzzle. It fits right into your organization's overall electronic waste management strategy. To see how it all connects, check out our guide on what is https://www.scientificequipmentdisposal.com/what-is-electronic-waste-recycling/.
Choosing Your Data Destruction Method: Wiping vs. Shredding
Figuring out whether to wipe or shred a hard drive isn't just a technical choice—it's a critical business decision that directly impacts your security, budget, and even your company’s green initiatives. There’s no single right answer. The best path forward depends entirely on your situation, from the type of data you handle to regulatory demands and your goals for asset reuse.
This decision is the foundation of your secure hard drive recycling workflow. It dictates whether a piece of hardware can be resold to recover value or if it absolutely must be turned into tiny pieces of metal to eliminate all risk. Getting this right is fundamental to a compliant and cost-effective IT asset disposition (ITAD) program.
When Data Wiping Makes Strategic Sense
Software-based data wiping, often called data sanitization, is pretty straightforward. Specialized programs overwrite every single sector of a hard drive with random data. When you do this using a recognized standard like DoD 5220.22-M, the original data is rendered unrecoverable, but the drive itself is left perfectly functional.
This is the go-to method when you want to get some value back from your old equipment.
- University Computer Lab Upgrades: Think about a university in Atlanta replacing hundreds of student lab computers. Those hard drives often have plenty of life left. Securely wiping them allows the school to resell the computers, turning what would be a disposal cost into a revenue stream for new equipment.
- Corporate Laptop Refresh Cycles: A national company with offices from California to New York refreshing its employee laptops can use certified wiping to get the devices ready for the secondary market. Or, they could donate them to a local nonprofit, which is a great look for their corporate social responsibility profile.
- Data Center Hardware Leases: When servers are returned at the end of a lease, data wiping is almost always a contractual must-do. It's how you clear proprietary data before the hardware goes back to the leasing company.
The biggest win for wiping is its role in the circular economy. You're extending the life of perfectly good IT hardware, cutting down on e-waste, and often generating a positive ROI—all without compromising data security for most business applications.
If you're interested in the technical side of things, our team put together a detailed guide on how to wipe a hard drive that walks through the entire process.
Why Physical Shredding Is Often Non-Negotiable
For some organizations, even the slightest chance of data recovery is a risk they just can't take. This is where physical shredding comes in. It is the final word in data destruction, providing an absolute, verifiable guarantee that the data is gone forever because the device it was stored on has been annihilated.
Shredding becomes the only logical choice in these high-stakes scenarios:
- Healthcare System Decommissioning: A hospital in Chicago retiring servers that held thousands of patient health records (PHI) is under immense pressure from HIPAA. Shredding isn't just an option; it's the only way to get total peace of mind and create a bulletproof audit trail.
- Government Agency Asset Disposal: A federal agency in Washington D.C. getting rid of drives with classified or sensitive information will almost always mandate physical destruction. It completely shuts down any possibility of espionage or data leaks.
- Financial Institutions Closing Branches: A bank closing a local branch in Austin has to destroy drives from ATMs, servers, and employee workstations. The reputational and financial damage from a potential data breach makes shredding a required security measure, not an optional one.
The process involves massive industrial shredders that apply sheer force to turn a hard drive into a small pile of metal fragments. At that point, data recovery isn't just difficult—it's physically impossible.
DoD Wiping vs. Shredding At A Glance
To make an informed choice, you need a clear look at the trade-offs. The right method is the one that aligns your security requirements with your operational and financial goals. This table breaks it down.
| Feature | DoD 5220.22-M Wiping | Physical Shredding |
|---|---|---|
| Data Removal | Data is overwritten and made unrecoverable by software. | Data and media are physically destroyed and unrecoverable. |
| Asset Reuse | Yes. The hard drive remains fully functional for resale or reuse. | No. The hard drive is rendered into scrap metal. |
| Security Level | High. Sufficient for most corporate and commercial data. | Absolute. The required standard for PHI, CUI, and top-secret data. |
| Cost | Generally lower, with potential for value recovery through resale. | Higher initial cost, with no potential for asset resale value. |
| Best For | IT refreshes, leased equipment returns, device donations. | End-of-life assets, damaged drives, HIPAA/Gov't compliance. |
In the end, many organizations find a hybrid approach works best. They wipe functional, lower-risk drives to recover value and shred the older, more sensitive, or non-functional drives to guarantee security. This balanced strategy really does offer the best of both worlds, optimizing your security, costs, and sustainability across your entire IT inventory.
On-Site vs. Off-Site Recycling: Which Is Right for You?
One of the biggest decisions you'll make is whether to handle hard drive destruction on-site or send it off to a secure facility. This isn't just about convenience—it's a choice that directly shapes your security protocol, your budget, and even your day-to-day operations. Whether you need local service or a nationwide rollout, understanding these options is key.
Getting this right means creating an unbreakable chain of custody. Getting it wrong can punch a hole in your entire data security posture. The right path depends entirely on your organization's risk tolerance and compliance demands.
This decision tree helps visualize the two main routes for data destruction, clarifying when wiping works versus when physical destruction is the only safe bet.
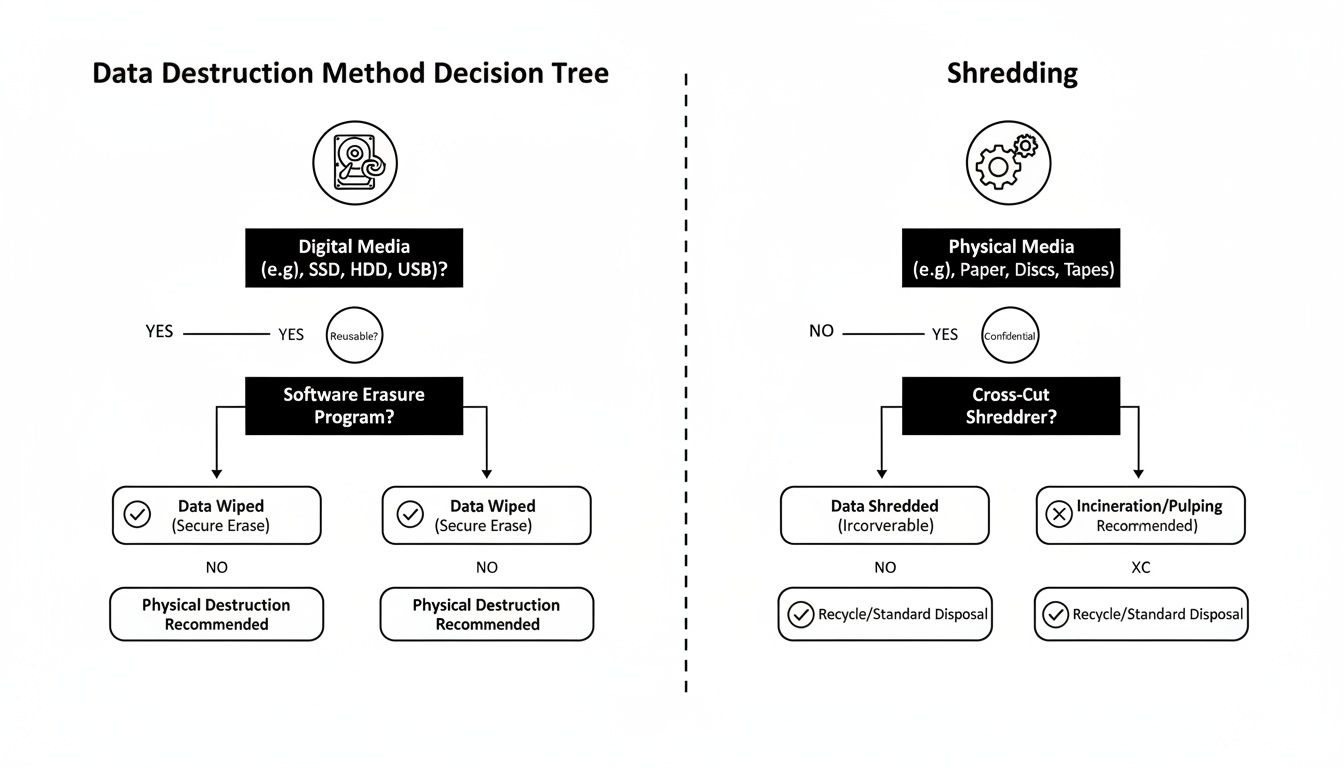
Ultimately, what you plan to do with the hardware—reuse it or retire it for good—is what really drives the choice between software-based wiping and good old-fashioned shredding.
The Case for On-Site Hard Drive Destruction
On-site destruction, usually done with a mobile shred truck right in your parking lot, delivers the highest level of security and transparency you can get. The whole process happens right at your facility, where you can watch every step.
For organizations handling extremely sensitive data, this is often the only acceptable method.
- Financial Institutions: A high-security bank in New York City isn't going to let drives full of financial data leave the premises intact. For them, witnessed on-site shredding is non-negotiable because it completely eliminates transport risk.
- Government Agencies: Any agency dealing with classified information or CUI (Controlled Unclassified Information) will almost certainly require on-site destruction to maintain a closed-loop chain of custody.
- Hospitals and Labs: To stay on the right side of HIPAA, healthcare providers in any city often opt for on-site shredding of drives containing patient health information (PHI). It provides maximum assurance and peace of mind.
The biggest win here is the unbroken chain of custody. You can physically watch as every single asset is scanned, logged, and fed into the shredder. You'll have a Certificate of Destruction in hand before the truck even pulls away.
When Off-Site Recycling Is the Practical Choice
While on-site is the gold standard for visibility, don't discount off-site recycling. A certified vendor can provide a secure, efficient, and often more budget-friendly solution for many businesses across the country. In this scenario, your drives are collected in locked, tamper-evident containers and moved in a secure vehicle to a specialized facility for destruction.
This workflow makes perfect sense for:
- Growing Businesses with Limited Space: A tech startup in San Francisco crammed into a shared office building probably doesn't have a loading dock for a massive shred truck. A scheduled, secure pickup is far more practical.
- Nationwide Decommissioning Projects: Imagine a large corporation shutting down dozens of offices across the country. Coordinating individual on-site shredding events would be a logistical nightmare. Centralizing destruction at a single, vetted off-site facility makes the whole project manageable.
Off-site recycling isn't less secure; the security is just managed differently. The process hinges on strict protocols like GPS-tracked vehicles, sealed containers, and documented handoffs at every stage. It's all about ensuring your assets are protected from your door to the final point of destruction.
The demand for both on-site and off-site solutions is booming, largely driven by the commercial sector. In fact, this sector makes up the bulk of the hard disk destruction equipment market, which is valued at over $450 million globally. Businesses are clearly prioritizing solid compliance and risk management. This isn't a niche service anymore—it's a standard part of responsible IT asset management.
Whether you're clearing out a single office or coordinating a massive equipment refresh, the right partner makes all the difference. Many organizations also find it helpful to bundle services and recycle electronics with a free pick up, which can streamline the logistics even further.
The Role of Documentation in Proving Compliance
Destroying a hard drive correctly is really only half the job. If you don't have a solid paper trail to back it up, your efforts are legally invisible. This leaves your organization wide open during an audit or, worse, a legal challenge. This isn't just about bureaucratic box-ticking; it's about creating verifiable proof that you met your obligation to protect sensitive information.
Think of it this way: if a data breach ever traces back to your organization, simply saying, "Oh, we shredded those drives," is not going to cut it. You need an ironclad, detailed record proving exactly when, where, and how every single asset was destroyed. This paperwork is your best defense against liability and a critical part of your overall security strategy.
The Certificate of Destruction Explained
The cornerstone of your defense is the Certificate of Destruction (CoD). This is much more than a simple receipt. It's a formal, legally recognized document that acts as your official record of compliant data sanitization. A valid CoD is your proof that you've successfully transferred liability for the destroyed assets to your certified recycling partner.
For a CoD to hold up under the intense scrutiny of a HIPAA or SOC 2 audit, it absolutely must include these non-negotiable details:
- A unique serial number for every single hard drive or storage device.
- The exact method of destruction used (e.g., DoD 5220.22-M wiping or physical shredding).
- Chain-of-custody details, including the final date and location of destruction.
- An official signature from an authorized person at the certified vendor.
A detailed Certificate of Destruction is your primary evidence of due diligence. It closes the loop on an asset's lifecycle and confirms your commitment to secure hard drive recycling protocols.
Creating an Unbreakable Audit Trail
The CoD is the final piece of a much larger documentation puzzle. To build a truly unbreakable record, you need supporting documents that track the asset from the second it leaves your control.
Let's imagine a law firm in Atlanta getting rid of old client hardware. Their process would generate a clear, auditable trail from start to finish:
- Serialized Asset Logs: Before the truck even arrives, the firm creates a detailed inventory list. They record the make, model, and serial number of every single server and computer being retired.
- Chain-of-Custody Forms: When the vendor arrives for pickup, they sign a form acknowledging they've received the exact assets on that log. This form tracks every handoff—from the firm's office, to the secure transport vehicle, and finally to the destruction facility.
- Final Certificate of Destruction: After the shredding is complete, the vendor issues the CoD. Crucially, this certificate cross-references the serial numbers from the firm's initial asset log, proving that every device they handed over was verifiably destroyed.
This combination of documents creates a powerful, end-to-end record. This kind of detailed, meticulous approach is at the heart of any professional security data destruction process. It shows you’re being proactive and compliant in managing sensitive data at every stage of its life.
How to Vet Your Secure Recycling Partner
Choosing the right partner for your hard drive recycling is easily one of the most important decisions you'll make in the entire IT asset disposition process. This isn't like picking an office supply vendor. The company you hire literally holds your organization's data security, compliance status, and public reputation in their hands.
A misstep here can lead to catastrophic data breaches, steep regulatory fines, and brand damage that’s almost impossible to reverse.
That’s why you have to look beyond a simple price comparison. In this business, the cheapest option is rarely the most secure. Your vetting process needs to dig into the qualifications that actually matter, making sure your partner operates with the highest standards of security, transparency, and accountability. This diligence is what protects you, whether you're a local clinic in Atlanta or a nationwide corporation managing assets coast to coast.
Look for Industry-Standard Certifications
Certifications are your first and most important filter. Think of them as independent, third-party proof that a recycler sticks to rigorous standards for data security, environmental responsibility, and worker safety.
Put simply, if a potential partner doesn't have the right certifications, they shouldn't even make your shortlist.
Two of the most respected certifications in our industry are:
- R2v3 (Responsible Recycling): This is a big one. It covers the entire lifecycle of electronic equipment, ensuring materials are handled in an environmentally sound way and that data security protocols are strictly followed.
- e-Stewards: Often considered the gold standard by environmental groups, e-Stewards enforces a zero-landfill policy and strictly prohibits exporting hazardous e-waste to developing countries. It also has incredibly robust requirements for data destruction.
When a vendor holds one or both of these, you know they’ve already gone through intensive audits. It's your baseline assurance of quality.
Scrutinize Their Data Security Protocols
Beyond certifications, you need to get into the nitty-gritty of how a vendor will handle your assets. A truly reputable partner will be an open book about their processes and will welcome your questions. Their answers should leave you feeling confident that they maintain an unbroken chain of custody from the moment your drives leave your facility to their final disposition.
To really vet a potential e-waste recycling company, you have to explore their procedures in detail.
Here are the critical questions I always recommend asking every potential vendor:
- "Can we audit your facility?" A confident, secure vendor will say "yes" without hesitation. The ability to do an on-site inspection (or at least a detailed virtual tour) is a massive green flag.
- "Show us how you track assets." They should be able to walk you through a clear, serialized tracking system that logs every single hard drive from the moment it leaves your possession. No gaps.
- "What are your employee security procedures?" Don't be shy about asking about background checks, security training, and access controls within their facility. The human element is often the weakest link in the security chain.
- "How are my assets secured during transport?" You want to hear about GPS-tracked vehicles, locked and sealed containers, and professional, uniformed personnel.
Any hesitation or vague answers to these questions should be a major concern. True professionals are proud of their security measures and are eager to prove their worth.
Verify Comprehensive Insurance Coverage
Finally, you absolutely must confirm the vendor carries the right kind of insurance. This is your financial safety net if the worst should happen. A standard business liability policy isn't going to cut it.
Insist on seeing a certificate of insurance that includes:
- Cyber Liability or Data Breach Insurance: This specific policy covers the immense costs that come with a data breach, like customer notification, credit monitoring, and legal fees.
- Errors and Omissions (E&O) Insurance: This protects you from claims of negligence or failure to perform professional duties, like a mistake made during the destruction process.
The coverage amount needs to be substantial enough to cover the potential financial fallout of a significant data breach involving your sensitive information. By thoroughly vetting potential partners on these three pillars—certifications, security protocols, and insurance—you can confidently pick a provider who will protect your data, your brand, and your peace of mind.
Sustainability Meets Security and Value Recovery

When you think about secure hard drive recycling, "destroy and dispose" is probably what comes to mind. But that's an outdated approach. These days, it’s a smart blend of data security, environmental responsibility, and financial strategy.
This isn’t about treating IT disposition as a cost center. It's about seeing it as a genuine opportunity.
A certified recycling partner does a lot more than just run your old drives through a shredder. They're your guarantee that hazardous e-waste stays far away from a landfill, which is a key part of building a real circular economy.
Bolstering Your Corporate Social Responsibility
When you work with a certified recycler, you’re making sure that the valuable commodities inside that shredded hardware are properly recovered. Instead of leaching into the ground as toxic waste, materials like aluminum, copper, and other precious metals get a second life back in the manufacturing supply chain.
This commitment to responsible e-waste management is a massive boost to your organization's corporate social responsibility (CSR) profile. It’s not just talk; it's a tangible action that shows customers and stakeholders you’re serious about protecting the planet.
The worlds of environmental sustainability and data security are finally colliding, and it's reshaping the entire industry. Modern systems can now recover up to 98% of strategic metals like platinum from obliterated SSDs while guaranteeing zero data recovery. This incredible efficiency creates new revenue streams that help offset recycling costs, a key factor driving a 27% boost in retention for integrated service providers. You can get more details on these advancements in hard disk destruction.
From Disposal Cost to Revenue Stream
The financial upside goes beyond just selling off recovered metals. Here’s a critical point: not every drive needs to be destroyed. For functional hardware that doesn't hold top-tier sensitive data, a certified DoD-compliant wiping is often the perfect solution.
This process completely sanitizes the drive, making it safe to be remarketed or redeployed within your own organization. What used to be a straight disposal cost now becomes a direct revenue stream. Suddenly, your IT asset disposition program is generating value while protecting your data, the environment, and your bottom line.
Common Questions About Hard Drive Recycling
When you get down to the brass tacks of data destruction, a lot of practical questions pop up. It's one thing to have a policy on paper, but making it work in the real world—whether for a single Atlanta office or a nationwide data center decommissioning—is another beast entirely.
Getting clear, straightforward answers is what bridges that gap. Let’s tackle some of the most frequent questions we hear from organizations every day.
Is Data Wiping Alone Enough for Compliance?
This is the big one, and the answer is: it depends.
For a lot of standard business equipment, a professional software wipe that meets the NIST 800-88 standard is absolutely compliant and sufficient. This is a great route to take if you plan on reusing or reselling the hardware. The drives are functional, but the data is gone for good.
However, when you're dealing with highly sensitive information, the game changes. Think patient health records (PHI) under HIPAA, classified government data, or critical financial information. In these high-stakes scenarios, physical destruction is often the only acceptable—and sometimes mandated—method. Shredding just removes all doubt.
Why Do I Need a Certificate of Destruction?
Simple: it’s your proof. A Certificate of Destruction (CoD) isn't just a receipt for a service rendered; it's a legally recognized document that proves you did your due diligence. It creates a complete, auditable paper trail that can be a lifesaver for compliance and liability.
Think of the CoD as your ultimate shield. If an auditor comes knocking or, worse, you're facing a data breach investigation, this single document—with its serialized asset lists and chain-of-custody details—is what demonstrates you took every required step to securely destroy that data.
What Happens After a Hard Drive Is Shredded?
The process doesn’t just stop with a pile of metal confetti. That would be an incredible waste. A certified, responsible recycler makes sure those shredded fragments get a second life.
- Sorting the Materials: First, the jumbled mix of aluminum, steel, circuit board pieces, and other metals is meticulously sorted.
- Back to the Supply Chain: These raw commodities are then sent to smelters, where they're melted down and reintroduced into manufacturing streams to create brand new products.
This is where true secure hard drive recycling comes full circle. You're not just completing a critical data security task; you're participating in a sustainable, circular economy that turns old liabilities into new resources.
At Scientific Equipment Disposal, we don't just give you services; we give you clarity and peace of mind. We provide secure hard drive recycling services locally and nationwide. We ensure your data is verifiably destroyed, your compliance is locked down, and your old hardware is recycled the right way. Find out more about our secure, sustainable disposal solutions at https://www.scientificequipmentdisposal.com.