A Guide to Secure and Compliant IT Equipment Recycling

When old tech piles up, it’s easy to think of it as just clutter. But for any organization—especially hospitals, universities, and government agencies—that pile of outdated electronics is a ticking time bomb of risk. IT equipment recycling isn't just about clearing out a storage room; it’s a critical function of risk management, data security, and corporate responsibility, whether you operate in a single city or have facilities nationwide.
The process involves much more than just hauling away old computers. It's about methodically dismantling and processing every device to recover valuable materials while ensuring hazardous components don't poison the environment. Most importantly, it requires secure data destruction to protect your organization's most sensitive information.
Why Smart IT Equipment Recycling Is Essential for Your Business
Let's be blunt: simply tossing old hardware in a dumpster or handing it off to an uncertified scrapper is a massive liability. For organizations handling patient health information, classified government records, or proprietary research, the fallout from improper disposal can be catastrophic.

Think about it. A single hard drive left in a retired server can hold thousands of confidential files. A data breach stemming from a discarded device can trigger crippling fines, lawsuits, and a loss of public trust that can take years to rebuild. Standard trash services just aren't equipped to handle this level of risk.
The Real Risks of Neglecting Proper Disposal
The danger goes far beyond data breaches. Electronic waste (e-waste) is packed with hazardous materials like lead, mercury, and cadmium. When this stuff ends up in a landfill, these toxins can seep into the soil and groundwater, causing long-term environmental damage.
This has led to a web of strict regulations that you can't afford to ignore:
- Data Privacy Laws: Regulations like HIPAA and GLBA don't just apply to live systems. They mandate secure data destruction for retired assets, with non-compliance penalties that can easily reach into the millions.
- Environmental Regulations: The EPA’s Resource Conservation and Recovery Act (RCRA) is clear. It establishes "cradle-to-grave" responsibility, meaning your organization remains legally liable for its e-waste, even after it leaves your facility.
- Brand Reputation: In an age where corporate responsibility matters, news of irresponsible dumping can permanently tarnish your organization's image and drive away clients, students, or patients.
The scale of the e-waste problem is staggering and growing fast. In 2022, the world generated roughly 62 million tonnes of e-waste, a figure expected to climb to 82 million tonnes by 2030. The scary part? Only 22.3% of that 2022 waste was properly collected and recycled, leaving a massive gap in responsible disposal.
Building a Secure and Compliant Framework
A well-planned IT asset disposition (ITAD) program turns this liability into a strength. It provides a structured, documented process to ensure every retired asset is handled securely, ethically, and in full compliance with the law.
For organizations in the Atlanta metro area and across the United States, partnering with a certified e-waste expert is the only way to guarantee peace of mind. A solid framework isn't just about dodging fines—it's about fundamentally protecting your operations.
Whether you're a university lab in Decatur, Georgia, or a national healthcare system with facilities from coast to coast, a clear recycling plan ensures your data and environmental duties are managed professionally. Our guide to corporate e-waste solutions dives deeper into building out these programs.
This playbook will walk you through everything you need to know to create a secure, compliant, and efficient asset disposition process that protects your organization from the ground up.
Preparing Your Assets for Secure Disposition
A successful IT equipment recycling project is won or lost long before a single device leaves your building. Getting your assets ready isn't just about making neat piles of hardware; it's a critical risk management step that establishes a secure chain of custody right from the start. Rushing this stage is a recipe for logistical headaches, incomplete paperwork, and glaring security gaps down the line.
When you properly prepare your equipment, you're setting the stage for a smooth, transparent, and defensible disposition process. For specialized organizations—think of a university laboratory in Norcross or a national research firm—this internal groundwork is non-negotiable for staying compliant and secure.
Building Your Disposition Inventory
First things first: create a detailed inventory of every single asset you plan to retire. This isn't just a quick headcount. It's a meticulous catalog that becomes the backbone of your entire project, acting as the manifest for your equipment's final journey.
This asset list serves as your single source of truth, capturing the essential details for each item. You'll need it for your own records, and your nationwide recycling partner will require it to do their job properly.
At a minimum, make sure your inventory sheet includes:
- Asset Tag Number: Your own internal ID for the equipment.
- Serial Number: The unique manufacturer's serial number.
- Device Type: E.g., Laptop, Server, Centrifuge, Monitor.
- Manufacturer and Model: For instance, Dell Latitude 7420 or HP ProLiant DL380.
- Physical Condition: Make a note of any major damage or if the unit doesn't power on.
This detailed log is what the Certificate of Data Destruction and final recycling reports are built on. These documents are your official proof of compliant disposal, so accuracy here is paramount.
Segregating Assets by Disposition Path
Not all retired equipment is heading to the same place. Some devices might still have significant market value, while others are destined for secure shredding. Separating them early on is a smart move that maximizes your potential return on investment and ensures security protocols are applied correctly.
Picture a government agency decommissioning an entire department. The IT team would physically separate the assets into distinct, clearly labeled groups.
- Group 1: Resale: Newer, fully functional laptops and servers. These are perfect candidates for data wiping and refurbishment, which can often generate a financial return for your organization.
- Group 2: Recycle/Destruction: Older, non-functional desktops, damaged hard drives, and any proprietary equipment that absolutely must be physically destroyed for security reasons.
This simple act of physical separation prevents costly mix-ups and makes the on-site verification process a breeze when the pickup team arrives. It guarantees that devices needing to be shredded aren't accidentally mixed in with items slated for remarketing.
Takeaway: The goal is to make the pickup process as efficient and error-proof as possible. Consolidate all assets in a secure, accessible location—like a locked storage room near a loading dock. This minimizes disruption to your daily operations and cuts down on the time your staff needs to spend overseeing the removal.
Final Internal Checks Before Pickup
Before your recycling partner shows up, there are a few final internal checks to tick off the list. The most important one? Confirming that all necessary data has been backed up from the devices being retired. While your disposition partner will handle the certified data destruction, the responsibility for preserving your data ultimately rests with you.
Once your backups are verified and your assets are inventoried and separated, you're ready for the next phase. This prep work is the first and most vital part of a seamless asset disposition process. You can see how these initial steps fit into the bigger picture by reviewing our detailed guide on how it works. Taking these measures ensures every piece of equipment is accounted for, secure, and ready for its journey.
Mastering Certified Data Destruction Methods
Once your assets are prepped, we get to what is arguably the most critical step for any hospital, lab, or government agency: data destruction. This isn't just about deleting a few files. True, certified IT equipment recycling depends on the verifiable, permanent elimination of every bit of data.
This process is a cornerstone of your risk management strategy. For perspective, the global e-waste management market is expected to jump from about USD 70 billion in 2024 to USD 81.27 billion in 2025. That rapid growth is fueled by new data privacy laws and ever-present cyber threats. For organizations like yours, proving that data from old hard drives and servers has been completely wiped is no longer just a good idea—it's a requirement.
This decision tree gives a good visual of the asset disposition pathway, helping you decide if an item is a candidate for resale or if it should be slated for recycling and destruction.
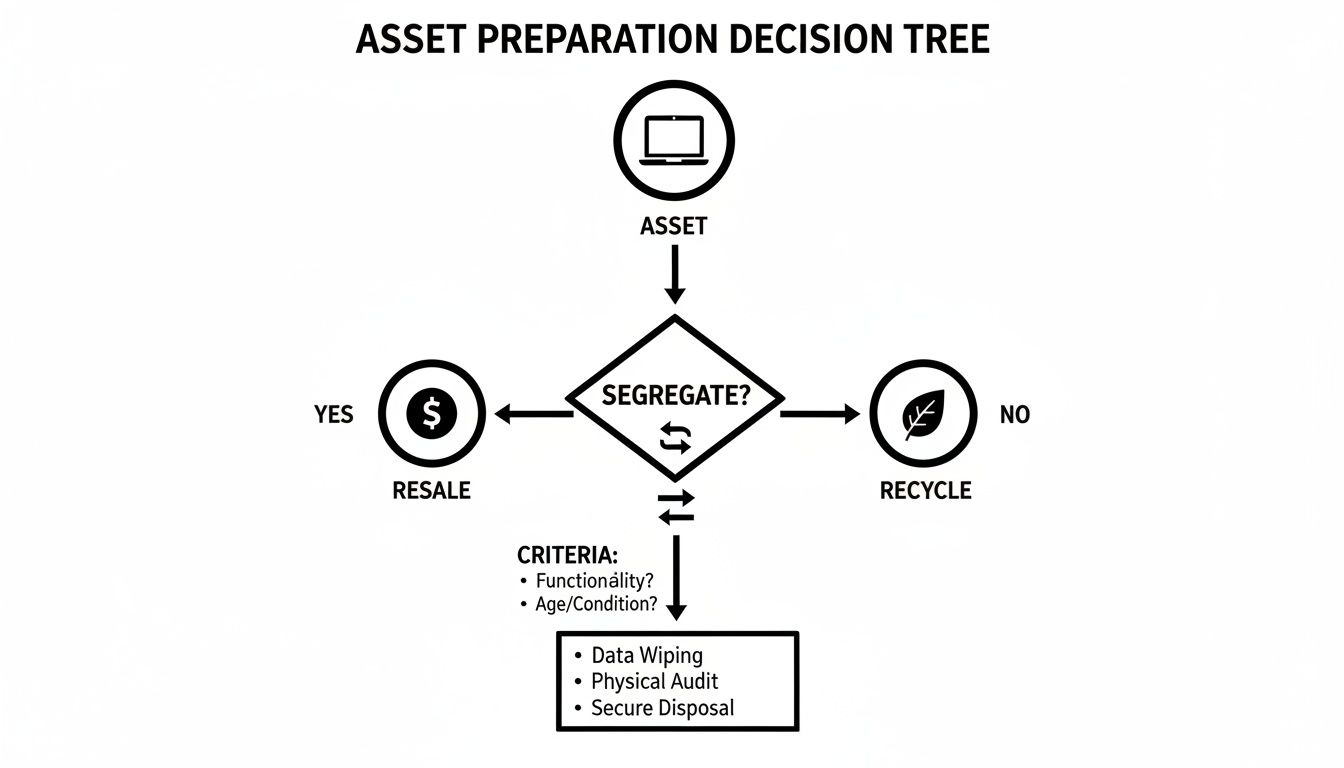
The key takeaway here is that how you sort your assets upfront directly influences which data destruction method you’ll use later on.
Understanding DoD 5220.22-M Data Wiping
One of the most trusted standards in our industry is DoD 5220.22-M. This is a software-based data sanitization method originally developed by the U.S. Department of Defense. It works by overwriting the data on a hard drive with specific patterns of ones, zeros, and random characters across three separate passes.
This triple-overwrite approach essentially scrambles the original information, making it virtually impossible to recover with any known technology. For organizations dealing with HIPAA, Sarbanes-Oxley (SOX), or other strict data regulations, this method provides a solid, auditable trail proving the data was professionally sanitized.
So when is data wiping the right move?
- When you want to preserve asset value: Wiping keeps the physical hard drive—and the laptop or server it lives in—intact and functional. This allows it to be refurbished and resold, which can generate a financial return to offset your recycling costs.
- For enterprise-grade equipment: High-value servers, storage arrays, and networking gear are perfect candidates for wiping and remarketing.
- For on-site security needs: Many certified partners, including us, can perform DoD-standard wiping right at your facility before the equipment even leaves the building, adding an extra layer of security.
Physical Destruction: The Finality of Shredding
While data wiping is highly effective, it's not the only tool in the shed. Physical destruction, most often done through industrial shredding, offers a different kind of guarantee. This process literally feeds hard drives, SSDs, tapes, and other media into a powerful shredder that grinds them into small, mangled pieces of metal.
There's no coming back from shredding. It is the definitive end for a data-bearing device.
Shredding is the go-to method in a few key scenarios:
- Damaged or Non-Functional Drives: If a hard drive won't even power on, software-based wiping is off the table. Shredding is the only way to ensure the data is destroyed.
- End-of-Life or Obsolete Media: For older, low-value devices where the effort to wipe them isn't worth it, shredding is often more cost-effective and secure.
- Maximum Security Protocols: Some organizations, particularly in government or R&D, have internal policies that mandate the physical destruction of all retired data media, no matter its condition or potential value.
A university research lab in Atlanta, for example, might have a damaged server drive containing years of proprietary study data. The drive itself is worthless, but the data is priceless. In this case, the risk of compromise far outweighs any minimal resale value, making shredding the only logical choice.
Choosing between wiping and shredding depends entirely on your specific security needs, the type of asset, and your compliance obligations. Here's a quick comparison to help guide your decision.
Data Destruction Methods Compared
| Method | Best For | Compliance Level (HIPAA, etc.) | Asset Resale Potential |
|---|---|---|---|
| DoD 5220.22-M Wiping | Functional, high-value assets (servers, laptops, enterprise drives) where value recovery is a goal. | High – Provides auditable proof of sanitization, meeting most regulatory standards. | High – Keeps the asset physically intact and ready for refurbishment and resale. |
| Physical Shredding | Damaged, non-functional, or obsolete drives; assets under maximum security protocols. | Highest – Offers irrefutable proof of physical destruction. | None – The asset is completely destroyed and only has value as recycled scrap metal. |
Ultimately, the right method ensures your data is gone for good while aligning with your financial and operational goals.
The Certificate of Data Destruction: Your Proof of Compliance
Whether you choose to wipe or shred, the process must end with one crucial piece of paper: the Certificate of Data Destruction (CoDD). This is a formal document issued by your recycling partner that serves as your legal and auditable proof of compliance.
This certificate is more than just a receipt. It's a critical legal document that should list the unique serial numbers of every single device that was sanitized or destroyed, tying directly back to your initial inventory. Verifying this document against your records is what closes the chain-of-custody loop. If an auditor ever comes knocking, that certificate is your definitive proof of responsible data handling.
To learn more about these protocols, you can explore our in-depth resources on certified data security.
Getting Your Equipment from Point A to B: Logistics and Secure Pickup
Once you've prepped your assets and figured out your data destruction plan, the next step is actually getting the equipment out the door. This isn't just a simple moving job; it's a critical security checkpoint in the entire IT recycling process. A professional, secure pickup is about more than just loading boxes. It’s a well-planned operation designed to protect your assets, ensure total accountability, and cause as little disruption to your work as possible.

This is where a true ITAD partner with nationwide capabilities really shows their worth. Whether you’re a hospital in downtown Atlanta trying to schedule a pickup on a Saturday to avoid patient traffic or a multi-state corporation coordinating logistics across several sites, you need the process to be seamless. That takes solid planning, clear communication, and a serious focus on security every step of the way.
Before the Truck Arrives: Coordination and On-Site Checks
A smooth pickup always starts with clear communication. Long before a truck shows up at your facility, your recycling partner should be working with you to nail down all the details. This means confirming your asset inventory list, understanding your building's specific access rules, and setting a firm pickup time that works for you.
When the uniformed crew arrives, their first task should be to verify the equipment against the inventory list you provided. This on-site validation is a crucial piece of maintaining the chain of custody. The team will match serial numbers and asset tags right there on your floor, making sure every single device is accounted for before it’s even touched. It’s a simple but vital step that prevents any mix-ups and confirms that what's leaving is exactly what you intended.
Tackling Common Logistical Headaches
Every organization has its own unique challenges. A high-rise corporate office in Midtown Atlanta has completely different logistical needs than a sprawling government complex in Decatur or a network of clinics across the Southeast. An experienced partner knows this and plans for it ahead of time.
- Hospitals and Clinics: Pickups almost always need to happen after hours or on weekends to avoid disrupting patient care. Discretion and efficiency are everything in these sensitive environments.
- Universities and Labs: It's common to have to coordinate with multiple departments, PIs, and campus facility managers. A good partner can handle that communication to streamline everything into one smooth pickup.
- High-Rise Offices: Access is often a puzzle of specific freight elevators, strict loading dock time windows, and building management rules. Pre-coordination is non-negotiable.
A professional ITAD provider doesn't wait for you to bring these things up. They'll proactively ask the right questions: "What are your loading dock hours?" or "Are there any special security clearances our team needs?" This kind of foresight is what prevents last-minute chaos and ensures the pickup goes off without a hitch.
Secure Transport and the Chain of Custody
After the inventory is confirmed, your assets are carefully packed and loaded into a dedicated, GPS-tracked vehicle. This isn't a job for a standard courier service. Your equipment should be the only cargo on that truck, eliminating any risk of it getting lost or mixed up with another company's assets.
The chain of custody is the unbroken, documented trail that follows your equipment from start to finish. It begins with your initial inventory, continues with the on-site verification and secure transport, and ends with the final reports you receive. This paper trail is your proof that every device was handled securely from the moment it left your control. When the truck arrives at the processing facility, the gear is checked in again, maintaining that continuous line of accountability. For any organization dealing with sensitive data, this meticulous tracking is absolutely essential.
When you're ready to arrange a pickup, having all your documentation prepared makes the entire process faster and more secure. You can see how these logistical steps come together when you schedule a secure pickup for your business. The process wraps up with the final documentation—serialized asset reports and recycling certificates—which officially closes the loop on your compliance duties.
How to Choose a Certified Recycling Partner
Picking the right vendor is probably the single most critical decision you'll make in this entire process. That choice directly impacts your data security, your compliance standing, and your environmental footprint. Whether you’re a hospital in the Atlanta metro or a nationwide research institution, the partner you select becomes an extension of your own risk management team. A simple handshake with a local scrapper just won't cut it anymore; you absolutely need a vetted, certified professional.
The stakes are just too high to leave it to chance. A vendor’s failure can quickly become your legal liability, which makes thorough due diligence non-negotiable. The right partner gives you something invaluable: peace of mind, backed by transparent, documented, and secure processes from the moment they arrive until the last asset is processed.
Non-Negotiable Vendor Certifications
Before you even think about looking at a price quote, you need to check for industry-standard certifications. These aren't just fancy badges for a website; they are hard-earned proof that a vendor follows rigorous, third-party audited standards for both environmental responsibility and data security. Honestly, think of them as the bare-minimum ticket to entry for any reputable nationwide provider.
Two certifications have become the gold standard in the IT asset disposition (ITAD) world:
- R2v3 (Responsible Recycling): This certification looks at the entire lifecycle of the equipment. An R2v3-certified recycler is required to track all materials to their final destination, which is your guarantee that hazardous e-waste isn't being illegally dumped overseas.
- e-Stewards: Developed by the Basel Action Network, e-Stewards is known for being incredibly strict. It includes an absolute ban on exporting hazardous electronic waste to developing countries, no exceptions.
Choosing a partner with either R2v3 or e-Stewards certification is your first line of defense. It’s the clearest sign that a vendor is committed to doing things the right way, protecting both your data and the environment.
The Ultimate Vendor Vetting Checklist
Once you've confirmed a potential partner has the right credentials, it’s time to dig a little deeper. Your goal here is to really understand their processes, their security protocols, and how they handle the downstream chain of custody. A reputable vendor won't just tolerate these questions—they'll welcome them and give you clear, direct answers.
Use this checklist to guide your conversations:
- Data Security Protocols: Ask them to walk you through their entire data destruction process, step by step. Do they use DoD 5220.22-M wiping standards? Do they offer on-site shredding for ultimate peace of mind?
- Sample Documentation: Request a sample Certificate of Data Destruction (CoDD) and a final asset disposition report. Look closely. Do these documents include individual serial numbers? Are they professional and easy to understand?
- Downstream Vendor Audits: This is a big one. Ask them how they audit their downstream partners (the companies they send materials to). A truly responsible recycler will have a documented system for vetting their entire supply chain.
- Logistics and Transportation: Find out if they operate their own fleet of secure, GPS-tracked vehicles for nationwide pickups. Just as important, do their drivers and technicians who handle pickups undergo background checks? This is vital for maintaining a secure chain of custody from your door to theirs.
- Insurance and Liability: Verify that they carry adequate liability insurance, including policies that specifically cover data breaches. This is your safety net in a worst-case scenario.
Finding a Partner Who Understands Your World
Beyond certifications and security protocols, the best partners simply "get it." They have real-world experience working with organizations just like yours, both locally and across the country.
A vendor who regularly services a hospital in Sandy Springs will already understand the unique challenges of HIPAA compliance and the need for discreet, after-hours pickups. Likewise, a national partner working with a university system will be familiar with handling specialized scientific electronics right alongside standard IT gear across multiple campuses.
The global electronics recycling market is projected to explode from USD 43.2 billion in 2025 to USD 147.9 billion by 2035. This massive growth is driven by the sheer volume of retired equipment, with PCs and laptops alone making up about 45% of it. This highlights just how critical the secure handling of these devices is for institutions like yours. When you're vetting a vendor, ask for case studies or references from clients in your specific sector—healthcare, education, or government.
Picking the right certified partner is the final, crucial step in protecting your organization. Taking the time to thoroughly vet your options ensures your sensitive data stays locked down and your organization stays compliant. Our overview of top electronic waste recycling companies can provide some additional context as you begin your search.
Common Questions About IT and Lab Equipment Recycling
Even the best-laid plans come with questions. When you're standing in front of a server room refresh in California or a lab decommissioning in Georgia, the details matter.
We get it. As a company based in Atlanta with a nationwide service footprint, we’ve handled thousands of projects for hospitals, labs, and universities across the country. Here are the practical, no-nonsense answers to the questions we hear every single day.
What Types of Lab and IT Equipment Do You Accept?
We handle a huge range of assets to make facility upgrades and cleanouts simpler, whether you're here in the Atlanta metro or anywhere in the USA. This includes all the standard IT gear you'd expect: servers, computers, laptops, monitors, and networking hardware like switches and routers.
But we also specialize in a wide array of lab equipment. We've seen it all, from centrifuges and analytical instruments to incubators and fume hoods. The easiest first step? Just send over your preliminary asset list. Our team will look it over and tell you straight up what can be recycled, what might have resale value, and if anything needs special handling.
How Much Does IT Equipment Recycling Cost?
The cost really depends on the project. It's a mix of factors like the volume and type of equipment, your logistics (do you need on-site services at multiple locations nationwide?), and the potential resale value of your assets.
For many projects with newer, enterprise-grade IT gear, the service can often be cost-neutral or even put money back in your budget through our remarketing program.
On the other hand, if you have older, obsolete, or broken electronics with no resale value, there’s usually a service fee. This covers the secure transport, certified processing, and responsible recycling. We always provide a clear, itemized quote upfront so there are no surprises. A huge bonus is that our certified DoD-standard data wiping is often included for free, which saves our clients a significant expense.
Key Insight: Don't automatically write off your old equipment as a disposal cost. We’ve seen many organizations pleasantly surprised when the value from remarketable assets covers the entire cost of the project. It can turn a liability into a budget-neutral—or even profitable—operation.
Is Your Data Destruction Process HIPAA Compliant?
Yes, 100%. Our entire data destruction process is built to meet and exceed the tough security rules of regulations like the Health Insurance Portability and Accountability Act (HIPAA).
For any data-bearing devices that are still functional and being considered for reuse, we follow the DoD 5220.22-M 3-pass sanitization standard. This is a software-based method that overwrites every bit of data, making it impossible to recover.
If a hard drive is damaged, too old, or you just need the absolute highest level of security, we offer physical shredding, either at your site or ours, anywhere in the United States. Once the job is done, you get a serialized Certificate of Data Destruction. This is your official, auditable proof that every single device was handled and destroyed according to industry regulations.
How Do I Schedule a Pickup for My Business?
Getting a pickup on the books is easy, whether for a single site or a multi-location project. It starts when you reach out to us with a quick overview of your project. If you have a list of the equipment, even a rough one, that’s a huge help.
From there, our logistics team jumps in to coordinate directly with you. We'll talk through any specific on-site challenges, like:
- Limited loading dock access
- Needing an after-hours or weekend pickup to avoid disrupting your operations
- Coordinating with building management or multiple departments across the country
Once the plan is locked in, we’ll schedule a firm pickup window using our own fleet of secure, GPS-tracked trucks. Our goal is to make the whole thing as quick and professional as possible, minimizing the work your team has to do.
Ready to put a secure and compliant recycling program in place for your organization’s IT and lab equipment? The team at Scientific Equipment Disposal specializes in creating solutions for hospitals, universities, and businesses across the Atlanta metro area and nationwide. We manage everything from secure logistics to certified data destruction, making sure your assets are handled responsibly from start to finish.
Get a transparent quote and simplify your next decommissioning project by visiting us at https://www.scientificequipmentdisposal.com.